The New Industrial Security Consulting Service from Pilz

April 24, 2024
How do you protect machinery against cyber attacks, misuse by operators, or manipulation? In the future, Industrial Security will be an important component of the EC Declaration of Conformity. The new Industrial Security Consulting Service from Pilz is your solution. Their experts analyse your risk with regard to security vulnerabilities on the machine, ad create an appropriate concept for greater cyber security, plus increased employee protection and machine availability.
ISCS – Industrial Security Consulting Service
Machine manufacturers and operators can only achieve comprehensive machinery safety with Industrial Security measures. These protect your machinery against cyber attacks, misuse by operators or manipulation, and are required by the Machinery Regulation for CE compliance. But how great is the risk of attacks to individual machinery, what might be the effects on health and safety at work and productivity, and which measures are sensible for reducing security vulnerabilities?
This is exactly where the Industrial Security Consulting Service from Pilz comes in: We analyse your risk with regard to security vulnerabilities on the machine, assess the individual hazard and likelihood of occurrence by levels, put together appropriate solution steps and check the measures taken. The ISCS helps to increase Cyber Security and makes sure that you correctly implement normative and legal specifications and are able to mitigate and avoid security incidents on the machine.
Four steps to a secure machine in accordance with Industrial Security:
The Industrial Security Consulting Service is made up of four modules that build on one another. After performing the individual steps, a regular re-evaluation of the Industrial Security status of the machinery is required in accordance with the moving target principle, in order to continuously counteract the latest cyber attack methods or vulnerabilities.
Benefits to you:
- Identification of potential risks and vulnerabilities
- Protection and strengthening against cyber attacks or incidents that stop production
- Increase employee safety, cyber security and machine availability
- Check risk-reducing measures for correct implementation
- Verifiable protection of the machinery in accordance with Industrial Security requirements
- Important component of the EC Declaration of Conformity
| The four steps of the ISCS | Benefits to you |
|---|---|
| 1. Protection requirements analysisIdentify the applicable standards and regulationsDetermine the limits of the system under considerationIdentify the protection objectives of each of the system’s assets, based on theexpected level of damage if confidentiality, integrity or availability is lost | Assess threat awareness |
| 2. Industrial Security risk analysisIdentify every risk for each asset within each life phase of the system, with regard to the considered protection goalsAnalyse existing risk-reducing measures and their effectRecommended approach for reducing riskDocument the vulnerabilities and the relevant hazard | Estimate the extent of the risk and need for action |
| 3. Industrial Security conceptDetermine the security level for each system sectionDefine and specify potential countermeasuresConsider availability and productivity Detailed assignment of security measures to identified risksCreate rules and guidelines for reducing the risk over the whole machine lifecycleDocument the requirements and implementation recommendations | Ability to plan countermeasures |
| 4. Industrial Security system verificationCheck the effectiveness of the measures implemented Produce a test report with information about the results and possible non-compliancesReview the documentation of the organisational measures | Liability protection due to compliance with relevant security requirementsIncrease employee protectionIncrease plant availabilitySave costs by defending against cyber attacksImage is protected thanks to effective preventative measures taken |
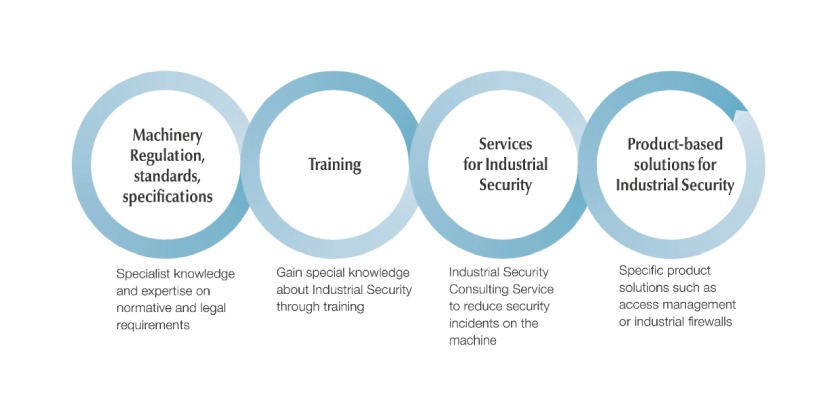
Industrial Security portfolio – Secure machinery, step-by-step
- Laws and standards for Industrial Security
- Training on Industrial Security
- Protect-related solutions for Industrial Security