Pilz: Access Management for Your Plant and Machinery

January 11, 2023
For comprehensive protection of your staff and optimum safeguarding of your machinery, you need a holistic safety concept, which considers aspects of both safety and security.
With the “Identification and Access Management” portfolio from Pilz, you are offered a comprehensive range of products, solutions and software for the implementation of safety as well as security tasks.
Below you’ll discover more about potential applications, from simple authentication to complex access permissions, and access management through to safe operating mode selection, maintenance safeguarding and safeguarding of data and networks.
Maintenance safeguarding system “key-in-pocket” for protection against unauthorised restart
This solution ensures that a machine cannot resume operation while people are still in the danger zone. The maintenance safeguarding system “key-in-pocket” is designed for machines with danger zones, which are protected by a safety fence and which staff need to access – robot cells for example.
In comparison with conventional lockout-tagout (LOTO) systems, maintenance safeguarding with the key-in-pocket solution is implemented via RFID keys with corresponding permissions and a safe list in the Pilz controllers. As a result, it provides a purely electronic restart protection and makes both mechanical interlocking devices and warning tags redundant.
And this is how it works:
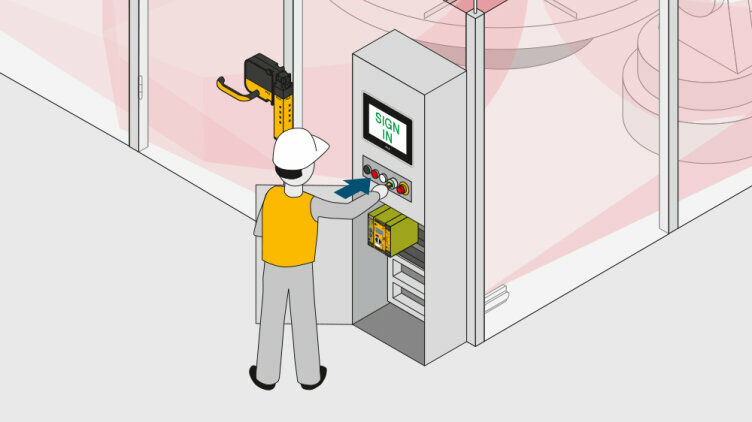
To access the plant, the operator uses their personal transponder key on the PITreader to authenticate themself on the safety gate.
The user’s permission is verified and, once successfully authenticated, their security ID is stored in a safe list in the Pilz controller (PNOZmulti 2 or PSS 4000).
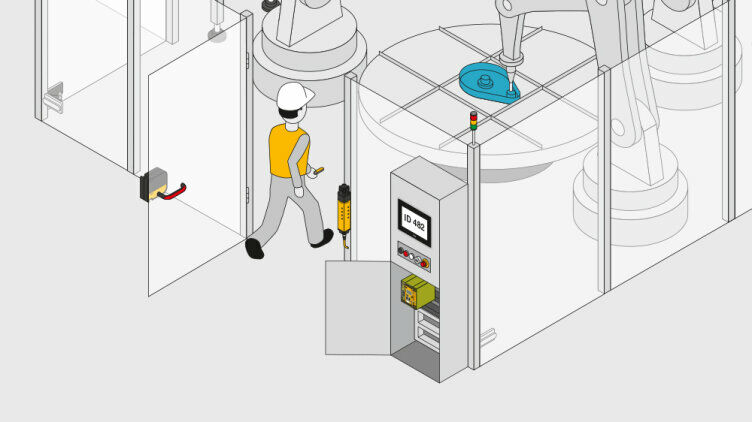
The machine can now be shut down, the safety gate opened and the machine accessed.
The staff member keeps hold of the transponder (“key-in-pocket”). Additional operators can sign in using their personal key in the same way and thus access the plant. Different safety gates may also be used for access.
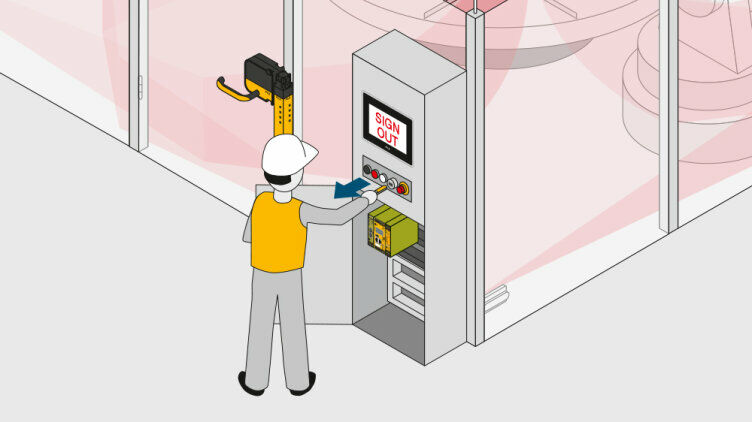
For the plant to resume operation, everyone must have exited the plant, closed the safety gates and used their personal key to sign out via the PITreader. The security IDs are removed from the safe list in the controller. Once the list is empty, the machine is enabled. Where plants are large with no overall view, there is an additional “blind spot check” in accordance with EN ISO 13849-1 5.2.2. This requires a visual inspection of the plant in areas that are difficult to see, before the machine can be restarted.
Your benefits at a glance with the “Identification and Access Management” portfolio
- Authentication of persons, safe restart protection
- Certifications: PL d Cat. 3 of EN ISO 13849-1, SIL CL 2 of EN 62061 and SIL 2 of IEC 61508
- Full control over which person has access to which machine, temporary permission also possible
- Simple to block, plus fast to reprogram when a transponder key is lost
- Considerably cheaper and more flexible as systems are made of metal
- Full traceability of who was in the plant and when (can be deactivated)
- Up to 20 people can access a machine at the same time
- Manual reset function, “blind spot check” in accordance with EN ISO 13849-1 5.2.2.
- Authorised personnel can delete the safe list, “key list reset”
- They do not need to exit the plant via the same door they used to enter